Reasons to be paranoid about the internet
OSI model implementation
Computer networks are organized in different layers with each layer performing a different function. These layers are best described in the OSI-model (see wikipedia: https://en.wikipedia.org/wiki/OSI_model#Layer_architecture) The function of each layer is performed by a protocol. To have a network stack that is easy to understand it is best that each protocol is constraint to a specific task limited to a layer of the OSI-model. The core protocols of the internet, as introduced by DARPA with ARPA-net, are TCP and IP. IP performs its function within the Network layer of the OSI model. TCP however covers 2 different layers of the OSI-model, namely the Transport Layer and the Session layer.
- Why did ARPA net not create 2 different protocols that each cover one layer?
- Why did the internet start with TCP/IP when there were plenty of other, and better protocol stacks available at the time?
- Why did DARPA, a US defense outfit decide to give away TCP/IP for free? Should no one be suspicious that the US government might have "defense" objectives by letting the world have this for free?
- Could it be that combining 2 layer functionality in one protocol was done to hide something additional that TCP can do? Something that serves DARPA's "defense" objectives?
HTTPS
Compared to HTTP most people think that this is just the same only that it encrypts what is being sent. There are more differences. A key one is that HTTP works over the TCP protocol whereas HTTPS completely skips the TCP protocol in favor of the UDP protocol. The difference between TCP and UDP is that TCP checks for complete delivery of the packet being sent, whereas UDP does not. So with HTTPS the server that sends the data does not check if it has been correctly received by your browser. This could make it easier for someone, somewhere in the middle change the data that is being sent (Man in the Middle attack)
- Why did HTTPS switch to UDP? It's hard to find correct information about this online and a lot of what you do still find about HTTS/SSL's use of UDB is very confusing. Even a Wireshark capture today got me confused as it claimed that HTTPS/SSL travels only over TCP today. I had to look up old Wireshark capture from 2023 for find a clear packet with HTTPS over UDP. Here's a link to screenshot from back then https_over_udp_in_2023.png.
- Why did the Clinton administration try to avoid the rest of the world outside the US from using SSL encryption 128-bit strong or stronger, the protocol that does the actual encryption for HTTPS? Were they afraid they would not be able to do such a man in the middle tampering if the encryption cypher were too strong?
CORS
Cross Origin Resource Sharing (CORS) is what makes it possible nowadays for a web page to load information from different URL's. Initially this was not allowed on the internet and when you load a page it could only contain information bits that came from the same url or IP-address. Some found this to too limiting so they invented CORS to define some rules built in the browser on what could be loaded from other URL's within the same web page. Today however CORS has been watered down to basically allow anthing to be loaded within a web page. This is dangerous for many reasons, but important to point out here is there is no longer a way to know for sure that the information you see visualized on a web page is fully coming from the URL in the address-bar of your browser.
- Why is it no longer important to know for sure that the information on a web page is coming from the URL you typed in?
- Who would like to change what's on your web page?
- Most web pages include trackers from google or meta. Has no one ever wondered that these included trackers could be used to completely rewrite your web page?
- Could there really be more secretive reasons behind the add-based business model that the likes of google use to give us all these things for free in exchange for personalized adds?
- Before HTML4 there were the HTML frames that actually made possible what CORS no does without limits, HTML3 frames did already allow to load content from a different URL in another frame in a way that made it quiet visaul. HTML4 depricated the "frame" tag and introduced the i-frame tag. Sure i-frames allow more fancy layouts, but why was it necesarry to no longer support the regular frame tag?
IPv6
Do you remember the craze that started in the early days of the internet where people were warning that the internet was going to run out of IP-addresses, this supposedly being a limitation of IPv4 and therefore a new versions seemed justified: IPv6. Back then it seemed obvious that IPv4 would be abondoned once IPv6 was fully rolled out so no one would run out of IP-addresses. IPv4 allows 4 billion public IP addresses. During that craze it seemed like every human on the planet was going to need his or her own IP address, but this is wrong. The IP-address you get from your ISP is always a private and multiple ISP's can use the same range of private IP-addresses. So the supposed shortage of IP addresses only really conserns servers on the internet.
- Were they (who could they be) ever thinking that we were going to have more than 4 billion servers connected to the internet?
- Today there are around 200 million servers connected to the internet with a unique IP address.
- So why did we need IPv6 when there was never going to be a shortage of IP-addresses with IPv4?
- IPv6 uses 128bit versus 32bit in IPv4. What kind of "spooky" functionality could be invented with these 96 extra bits?
BigTech's extranets largely replace the internet
The Big Tech companies like Google, Apple, Meta, Microsoft, have also been getting paranoid about the internet for many years. So as creative as they are they decided to do something about it. They actually built out their own internal companynetwork's the the front-door of nearly every ISP in nearly all countries. With the exception of Apple all these Big tech companies own 10 to 20 cross-ocean fiber cables. This has not only been to interconnect their own regional data centers but they also use this to expand their connection to the public internet to multiple points where possible directly to to the local internet back bone provider or even directly to a local ISP. In effect for all traffic going from your computers or devices to say Google, if your ISP connects directly to Google's extranet, you completely bypass the public internet alltogether. This in itself is not necesarrily a problem, but if you start to think about what I explained above about CORS, Google's servers are not just called when you type a url that ends on ...google.com, they are also called by cookies and trackers from just about every other web site you visit. This potentially gives companies like Google the power as explained to rewrite (e.g. with java-scripting) any web site that includes a call to Google.
- Do you think it is a good idea to give Big Tech companies the power to control everything you do on the web?
- Do you think that Big Tech companies get enough oversight so they themselves or who knows a third actor, like the state or some secret global org you only hear about in conspiracy stories (e.g. NWO) would hijack that Big Tech companies hook into all your web content for "evil" reasons?
- Then there's the CDN's, the Content Delivery Networks that are not big tech, but mid-size tech. Think of companies like Akamai and Cloudflare. CDN's deliver content locally that they cache in your region so it doesn't have to come from far away across an ocean. Most Big Tech companies are no longer using one of the independent CDN's, they started to build their own. These Big Tech companies also sell CDN services to others, making you ever more dependent on this direct ISP to BigTech network connection that bypasses the internet not just when you type ...google.com but also ...anywebsite.com that uses Google's CDN. This gives tremendous, potential power to these companies. Still after 30 years of internet, it is also no small accomplishment that no single of them has tried to really abuse that power. Innovation, ethics and values are still essential for ensuring continued success for any Big Tech company. Why don't companies like Google start their own competitor to the internet, they have most of the infrastructure ready for this?
5G and net-neutrality
It shouldn't always be me explaining, so here is what GrokAI writes in it's conclusion: 5G does not inherently violate net neutrality, but its network slicing feature enables ISPs to prioritize certain traffic, creating fast lanes that can conflict with the principle of equal treatment. Commercial incentives, regulatory ambiguities, and the potential to widen digital divides exacerbate these concerns. While some argue that 5G’s capacity and efficiency could neutralize neutrality issues, critics highlight that finite bandwidth and ISP practices (e.g., throttling, paid prioritization) undermine this optimism. Without clear regulations, 5G’s capabilities risk creating a tiered internet, contrary to net neutrality’s goals.
5G network slicing can target individual users for both throttling and blocking by leveraging user-specific policies, DPI, and dynamic slice management. This is enabled by 5G’s granular control mechanisms (e.g., NSSF, UPF, PCF) and poses a significant threat to net neutrality by allowing ISPs to discriminate against specific users based on subscriptions, behavior, or commercial interests. Regulatory gaps, especially in the U.S. post-2025, exacerbate the risk of abuse, while commercial incentives drive ISPs to prioritize premium users or services
In my words: where there was previous never a network standard that included the possibility to split up traffic in fast and slow lanes, this is now possible with 5G. This goes against the principle of net-neutrality on the internet where your ISP does not decide, nor anyonwe else, which of your internet traffic goes fast and which slow. This not only can be used by the ISP to decide what's fast or slow, governments or other stake holders may want a say. Quickly this turns into a political debate with concerns about censurship, free speech and then the question arrises: We need rules on how to make the rather politially sensitive decision on how to use this feature of 5G. If you ask me this was a dum idea to add this feature to 5G. It goes against the principles and values of of the free internet and if someone actually decides to use this slicing feature of 5G and launch a political debate because of it it could even slow down the implemntation of 5G.
But hold on, off course no one will want to use this in the beginning because of possible politice. But what if where 5 years in the future and 5G is old, 4G, 3G do no longer exist and at 6G is a newer version of 5G with the same slicing feature. What if someone really comes up with a single rule that all ISP's need to implement? Why? Who?
- Imagine a society with a social credit system where you get punished for bad behavior, such as crossing the road when there's a red light for pedestrians. The camera on the traffic light does a face recognition of you and as a punishment, all your internet streaming services get blocked (possible with 5G). Instead, you must confess on 4 different social networks, under your own account, that you crossed the street when there was a red light. Only after blaming and shaming yourself publicly 3 times for 2 weeks, your access to streaming services is restored over 5G.
- Imagine a society where, like in conspiracy stories, there is a global secret organization trying to take over the world (e.g., #NWO) to install authoritarian, fascist dictatorship with absolute control over all information. Only true believers in this dystopia are allowed privileged access to information like Wikipedia. Everyone else gets standard propaganda over all news outlets they control. 5G could be used to regulate who gets more access than the normal folk. Sometimes the normal folk get access to Wikipedia, but only for 1 hour each week. At that time, everyone tries to access it at the same time over 5G's slowest lane, making it painstakingly slow and you have to be lucky to load 2 web pages in that 1h a week on wikipedia.
- In a totalitarian society the fact that 5G is always used on a device that can only be used by a single person, it's your phone, with your sim card and your phone number, can also be seen as a further tool to control access to information. Imagine a society where wired home internet (DSL or Fiber) gets banned and the only internet access there is is cellular. Even Wi-Fi would be banned. This would give this slicing and blocking feature from 5G today an even greater powerful tool for an oppresive regine.
5G is defined by the 3GPP consortium of vendors, telcos, ... Some of the main advocats of slicing were American telco's AT&T and Verizon who gave as reason that they want to give fast access to premium customers. This is a false arguments. The previous standard 4G already allows speeds of up to 3Gbps, that is faster then a standard 1Gbps Ethernet cable that plugs into your computer. Why do we need internet on our phones to be faster then on our computers? Will we soon have 8K video on a 7inch phone display. Maybe there's a future where we will want to watch our phones under a microscope so we get to see how many pixels we otherwise really could never ever see with human eyes (joking).
Please care about net-neutrality, it's about your rights, your freedoms. Don't be indifferent, this really matters. We only get to have our rights and freedoms as long as we keep reminding ourselves that many who came before had to fight to get them and that the day might come where we, yes we, might have to fight again to defend the freedoms and rights we before a silent, indiferent majority lets it all be taken away.
Freedom for the internet business model chained to adds and not so free information and services
Personalizatoin and Tracking on the internet today is often hidden and unclear or obfuscated. In most cases it is used to gather data about users and analyze it. These activities that most websites on the net perform are often not required to provide the service they adverise. However it may currently be needed as part of the often equily obfuscasted business model used to monetize the offered service.
I am now convinced that such illusize data gathering + analysis ativities about:
Such activitieis should be banned.
Keeping the status quo is not only detremental for democracies as we have seen for instance around the Facebook scandals during US elections of 2016 as well as the UK's Brexit election. Also other, non-democratic forms of government should start to understand that also for them the current way the internet works will become subversive, be it in a different way then what they have seen in the past.
Regardless of which form of government or how it relates to its local as well as global economy and businesses, we see that today everything evolves around user engagement. Without user engagement in the high numbers as a company you do not exist is today's perception and often key for business model. This makes it only normal that number of clicks, seconds you spend reading an article or looking at an image are all captured to understand how and how long you as a user are engaged with the information or service offered. Personalization helps getting more user engagements but this is where the things go wrong because more and more users are not just being categorized into a group but their personalities, their feelings are now being manipulated so that their are made to fit certain categories that are more easy exploit into the web sites business model. Over time this will lock people up into their unique personalization space whether from which they may no longer be able to escape.
User engagement on its own and the strive to get more of your attention should not by itself be destructive to society. The problem comes from its inevetable combination with trying to provide improvements tailered to the individual through personalization of content. With such a high incentive to get more engagement this personalization which may at one point have been well intended is now becoming more and more a way to mold users into specific groups for which it is well known how to use them. Often sites will provide suggestions to
More topics to get paranoid about
Let me know if you find this interesting and if you would like me to further detail the list of reasons to get more paranoid about the internet:
- Has avg latency really gone up everywhere?
- Chrome/webkit
- Nothing that guarantees authenticity
- Internet is a monopoly
- What is there on the net that you cannot spoof
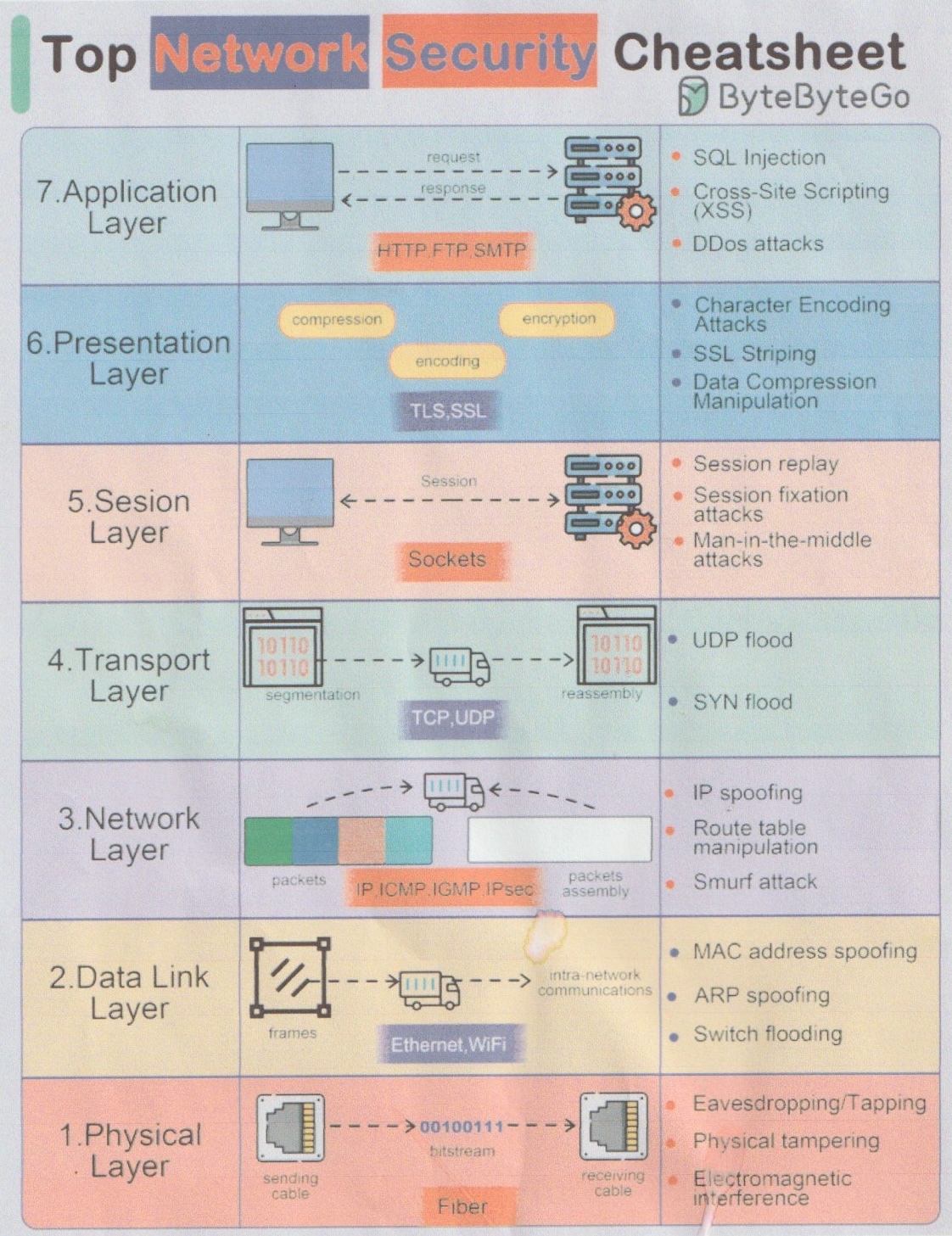
List of internet hacking vulneratbilities placed on OSI-model
The diagram below lists for the internet protocol stack what are well known vulnerabilities and ways of hacking the internet for each layer of the OSI-model. I'm not an expert in hacking, but this gives a good view on how vulnerable the internet really is at every level. Why is so little being done to fix these security vulnerabilities I keep on asking?
This article was originally published on August 23rd 2025 on my site here: https://splendid-treacle-0df202.netlify.app/article_reasons_to_be_paranoid_about_the_internet
